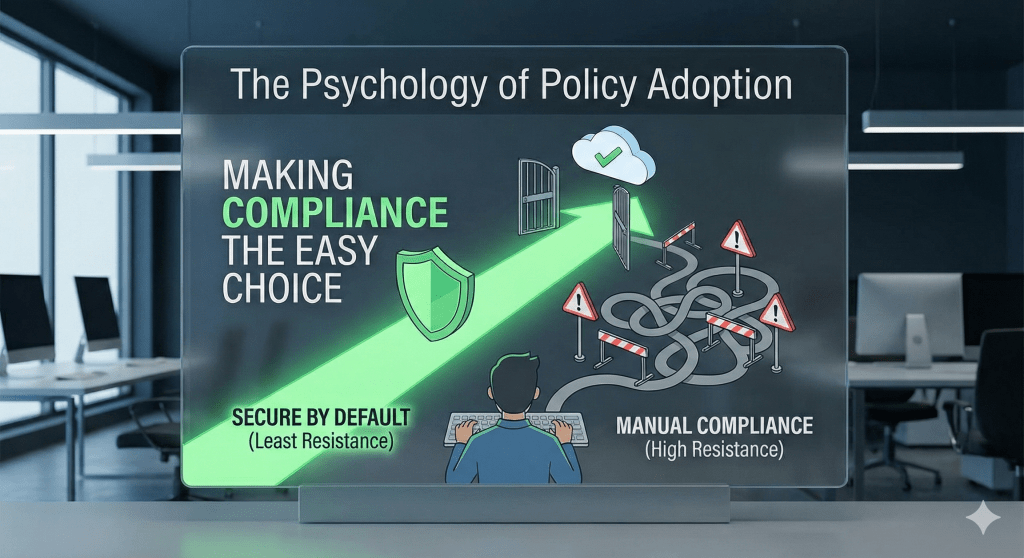
How to Make “Secure by Default” the Path of Least Resistance for Developers
In every organisation, security and compliance leaders talk endlessly about policies. But policies don’t protect an organisation.
Behaviour does. And behaviour is shaped by incentives, friction, context, and psychology not by documents in Confluence.
The truth is simple: You can write the most beautiful policy in the world, but if it creates friction for developers, it will be bypassed, ignored, or quietly “worked around.”
So the real question every CAIO, CISO, CDO, and CCoE must ask is:
How do we make secure behaviour the default behaviour?
Not enforced. Not negotiated. Not begged for. Default.
Let’s break down the behavioural science behind policy adoption and how to engineer a culture where compliance becomes the easiest path, not the painful one.
1️⃣ Security Fails When It Feels Like Punishment
Developers don’t resist security because they don’t care. They resist because:
- Controls add time
- Approval gates delay delivery
- Templates are unclear
- Tools are inconsistent
- Documentation is outdated
- Policies are written in legal jargon
From a psychological standpoint, this triggers:
- Friction
- Fatigue
- Loss aversion
- Defensive behaviour
Once developers associate security with “pain,” they naturally gravitate toward shortcuts.
The solution is not stricter enforcement. The solution is removing the pain.
2️⃣ Compliance Works When It’s Invisible
The most secure organisations in the world don’t treat policies as things you “apply.” They treat them as things you don’t even notice.
This is the essence of:
“Secure by Default”
Controls are built into:
- CI/CD pipelines
- Cloud templates
- Infrastructure scaffolding
- API gateways
- Data platform defaults
- Identity providers
- Model lifecycle workflows
If developers can deploy quickly without making choices that risk the organisation, you have achieved psychological alignment.
The secure path becomes the fastest path.
3️⃣ Make the Secure Path the Path of Least Resistance
This is a principle from behavioural economics:
“People will almost always choose the option with the lowest cognitive load.”
So, design compliance to be:
- Automatic
- Embedded
- Pre-approved
- Opinionated
- Tool-driven
- Idiot-proof (in a respectful way)
- Provided by default, not manually invoked
Examples:
✔ Pre-approved cloud blueprints
A developer chooses “Service A Template,” and:
- IAM is already correct
- Encryption is default
- Logging is enabled
- Data residency is enforced
- Secrets are handled by vaults
No negotiation. No guesswork.
✔ Guardrails-as-Code
Instead of PDF policies, controls are implemented as code in CI/CD.
✔ One-click landing zones
Compliance built into the platform itself.
✔ Automated policy checks
Developers get instant feedback inside their tools — not from email escalations 3 weeks later.
In psychology, this is called friction reversal: Redirect effort away from risky behaviour and towards secure behaviour.
4️⃣ Policies Should “Feel Like” Tools — Not Rules
A policy document does not change behaviour. A tool does.
The modern enterprise must shift from:
❌ Writing policies to
✅ Productising policies as developer experiences
This is the mindset shift behind:
- Secure-by-default platforms
- Data governance automation
- CCoE guardrail libraries
- Policy-as-code
- AI governance baked into pipelines
- Semantic rules encoded into toolchains
If your controls are not usable, they are not enforceable.
5️⃣ Developers Adopt What They Trust Not What They Fear
Fear-based compliance (audits, escalations, penalties) creates adversarial behaviour.
Trust-based compliance (clarity, speed, consistency) creates partnership.
Developers follow policies when:
- They understand why a rule exists
- The rule protects them from future incidents
- The rule improves reliability
- Following the rule gets them to production faster
The psychology is clear: Compliance works when developers see it as a productivity enhancer, not a blocker.
6️⃣ Culture Is the Final Multiplier
You can enforce controls through tooling. But culture determines whether they endure.
Create a culture where teams say things like:
- “We don’t deploy unless tests pass.”
- “We use the standard blueprint — it’s safer.”
- “Let’s check the data lineage before we ship.”
- “Security is just part of shipping quality.”
This is the psychology of internal norms.
When developers peer-pressure towards compliance, your job is done.
7️⃣ Final Thought: Make Good Behaviour Effortless
The endgame of policy adoption is not education. It is effort elimination.
Don’t ask developers to remember 200 rules. Build environments where breaking rules is impossible and following rules is automatic.
This is the future of enterprise governance:
- Invisible
- Embedded
- Tool-driven
- Behaviourally designed
- Human-centric
- Secure by default
If you want a secure organisation, don’t write more policies.
Design a system where the secure thing is the easy thing — and the easy thing is the only thing.
#CloudGovernance #AIGovernance #SecureByDefault #PolicyAsCode #DevSecOps #PlatformEngineering #DeveloperExperience #BehaviouralScience #EnterpriseSecurity #Leadership #DigitalTransformation
Leave a comment